Have you ever need to access your servers in virtual private cloud environment outside from “safe-zones”? Moreover, does your team willing to login on those machines from almost anywhere at the least appropriate times? And all this requires Volvo-Class security? Well, we got you covered.
Since this article focus on AWS, our challenge comprehends Two major concepts.
- Enabling the content of landing pages via S3 endpoint in addition to IP white listing.
- Making sure no one routes internet traffic through the cloud network yet without losing connectivity.
Before telling more, let’s assume a basic scenario; you’ve launched a t2.nano instance & started an openvpn server (with docker or not) and you created a security rule which allows your openvpn instance’s Elastic IP address to any machine in the vpc as well as your S3 buckets. Sounds great but not very ideal. The thing is, AWS doesn’t cost a penny for the network traffic inside your VPC. So from going one EC2 to another you have to reach it over internet. That means both cost and speed issues. Same rule applies for your buckets surely. Not even mentioning that you are also providing kind of an open source ZenMate solution to all your users because whatever they download or upload goes through your network and your very own encrypted connection. And that is something no system administrator wants to be responsible for.
So what is the exact solution? Obviously it isn’t to block outgoing traffic for 0.0.0.0/0 and I can assure you, we have tried countless approaches from config files to kernel parameters. Meet the most elegant way now, OpenVPN-AS
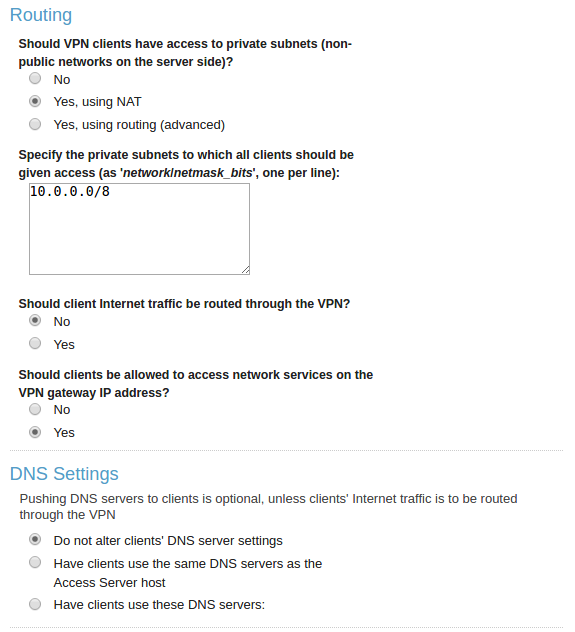
As you can check the page under Configuration > VPN Settings right after installing the access server, you can specifically state that your clients must reach only internal network CIDR (in this case ours was in pic) through vpn routing connection and not the whole Internet. When you check after establishing connection you will see your IP remains the same but your routing table has few more lines now. On EC2 every instance has unique internal ip address and by using them you can jump any server that your credentials exist. To do this in an easy way, you can always keep a record of your instances’ both internal and Elastic IPs in AWS Route53 service. Keep in mind that if your current LAN also uses the same ip-block you will only be able to connect AWS during the vpn session and not to the computer on your right. Another consideration might be, on the free subscription, OpenVPN-AS supports 2 concurrent connections at a time without any user number limit in total.
This brings us the other subject, S3 Endpoint. Below you will see an example policy that covers white-listing & endpoint rules together. Beware bucket name is called “my.examplebucket.com”.
{
"Version": "2012-10-17",
"Statement": [
{
"Sid": "EndPointAccess",
"Effect": "Allow",
"Principal": "*",
"Action": "s3:GetObject",
"Resource": [
"arn:aws:s3:::my.examplebucket.com/*",
"arn:aws:s3:::my.examplebucket.com"
],
"Condition": {
"StringEquals": {
"aws:sourceVpce": "vpce-XXXXXXX"
}
}
},
{
"Sid": "IpAccess",
"Effect": "Allow",
"Principal": "*",
"Action": "s3:GetObject",
"Resource": [
"arn:aws:s3:::my.examplebucket.com/*",
"arn:aws:s3:::my.examplebucket.com"
],
"Condition": {
"IpAddress": {
"aws:SourceIp": [
"XXX.XXX.XXX.XXX/32",
"YYY.YYY.YYY.YYY/32"
]
}
}
}
]
}
Make sure you have attached corresponding outbound security policy to your vpn instance. After enabling endpoint service, you can find it’s destination ID on RouteTables under VPC managment console. After everything is done, it should look like this
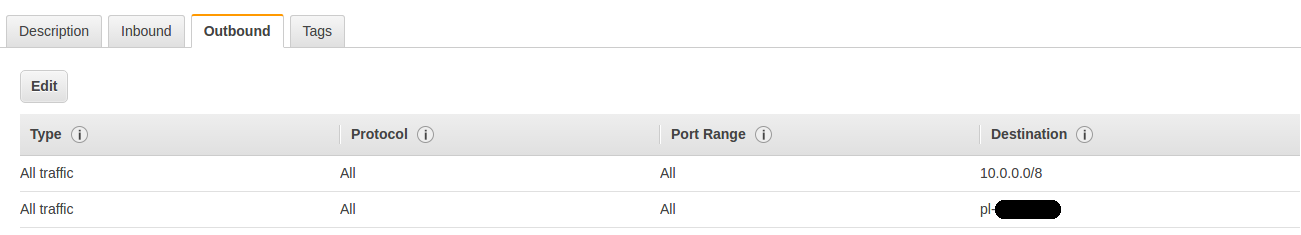
You should also keep in mind that at time being AWS doesn’t support endpoint access over peering connections. Which means if you have multiple AWS accounts or regions connected each other over peering setup, you won’t be able to get the S3 content from those, even if you specify the correct bucket policy. Therefore you might need to keep your buckets with the same habitat where your beloved vpn instance actually runs on. It’s rather cost effective and easy to manage after all. Hope you gain a good grasp of this seems-small-but-deals-big problem.